Posted in
Exchange Server |
6 Comments | 29,407 views | 30/08/2010 21:10
At the part 2, we configured mailbox databases. Also we made them high available with Exchange DAG.
Now at this part will see how to configure OWA load balancing and Certificate. I’ll use Citrix Netscaler for all load balancing requirements but you can use other hardware load balancing solutions like Brocade or software solutions. Idea is same for all nlb solutions :)
As the first part, I’ll load balance Exchange OWA.
Add your first CAS server as a service in Citrix.
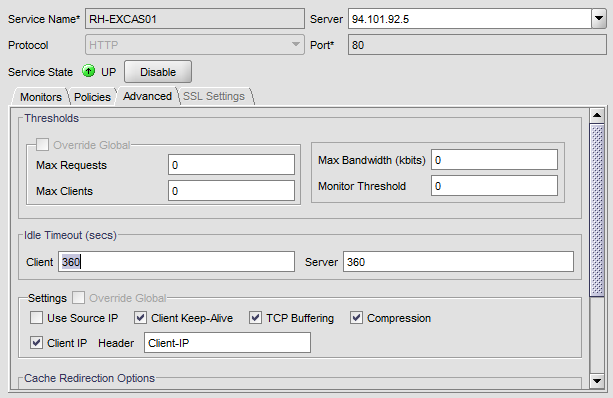
Do same thing for the second CAS Server.

Now, go to EXCAS01 and create certificate request for OWA.
Lets see default certificates:
Get-ExchangeCertificate -Server 'EXCAS01' |
Get-ExchangeCertificate -Server 'EXCAS01'

So create your certificate request on EXCAS01:
New-ExchangeCertificate -FriendlyName 'exchange.radore.com.tr' -GenerateRequest -PrivateKeyExportable $true -KeySize '2048' -SubjectName 'C=TR,S="Metrocity",L="Istanbul",O="Radore Hosting",OU="IT",CN=exchange.radore.com.tr' -DomainName 'exchange.radore.com.tr','autodiscover.radore.com.tr','EXCAS01','EXCAS02','EXGW01','EXGW02' -Server 'EXCAS01' |
New-ExchangeCertificate -FriendlyName 'exchange.radore.com.tr' -GenerateRequest -PrivateKeyExportable $true -KeySize '2048' -SubjectName 'C=TR,S="Metrocity",L="Istanbul",O="Radore Hosting",OU="IT",CN=exchange.radore.com.tr' -DomainName 'exchange.radore.com.tr','autodiscover.radore.com.tr','EXCAS01','EXCAS02','EXGW01','EXGW02' -Server 'EXCAS01'
Buy your commercial certificate and save certificate code to C:\cert.txt.
Import your certificate on EXCAS01:
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path C:\cert.txt -Encoding byte -ReadCount 0)) -Password:(Get-Credential).password |
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path C:\cert.txt -Encoding byte -ReadCount 0)) -Password:(Get-Credential).password
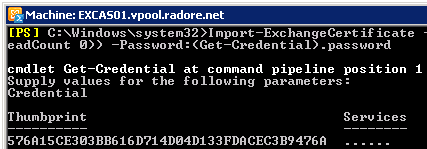
Assign IMAP, POP and IIS services to certificate. Don’t forget to use your own Thumbprint.
Enable-ExchangeCertificate -Server 'EXCAS01' -Services 'IMAP','POP','IIS' -Thumbprint '03BB616D714D04D133FDACEC3B9476' |
Enable-ExchangeCertificate -Server 'EXCAS01' -Services 'IMAP','POP','IIS' -Thumbprint '03BB616D714D04D133FDACEC3B9476'
Lets check certificate status again:
Get-ExchangeCertificate -Server 'EXCAS01' |
Get-ExchangeCertificate -Server 'EXCAS01'
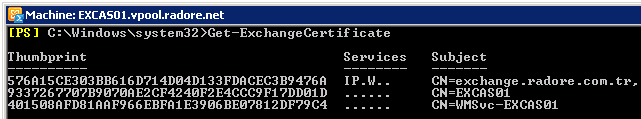
As you see, services are assigned to new SSL certificate.
We will export our certificate and import it to second CAS server, EXCAS02.
1
2
| $File = Export-ExchangeCertificate -Thumbprint '03BB616D714D04D133FDACEC3B9476' -BinaryEncoded:$true -Password (Get-Credential).password
Set-Content -Path "C:\htcert.pfx" -Value $File.FileData -Encoding Byte |
$File = Export-ExchangeCertificate -Thumbprint '03BB616D714D04D133FDACEC3B9476' -BinaryEncoded:$true -Password (Get-Credential).password
Set-Content -Path "C:\htcert.pfx" -Value $File.FileData -Encoding Byte
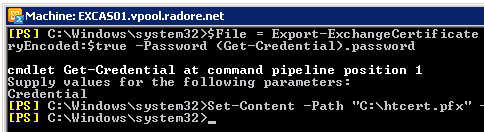
Now, transfer your pfx file to EXCAS02 and import it:
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path c:\htcert.pfx -Encoding Byte -ReadCount 0)) -Password:(Get-Credential).password -PrivateKeyExportable $true |
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path c:\htcert.pfx -Encoding Byte -ReadCount 0)) -Password:(Get-Credential).password -PrivateKeyExportable $true
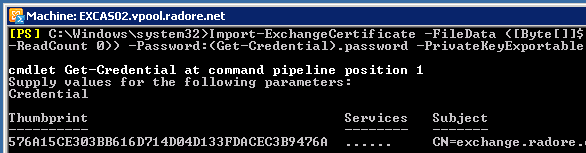
Lets check certificate status again:
Get-ExchangeCertificate -Server 'EXCAS02' |
Get-ExchangeCertificate -Server 'EXCAS02'

Enable same services for EXCAS02:
Enable-ExchangeCertificate -Server 'EXCAS02' -Services 'IMAP','POP','IIS' -Thumbprint '03BB616D714D04D133FDACEC3B9476' |
Enable-ExchangeCertificate -Server 'EXCAS02' -Services 'IMAP','POP','IIS' -Thumbprint '03BB616D714D04D133FDACEC3B9476'
Now import same certificate to Citrix Netscaler. Navigate to SSL and click import PKCS#12.
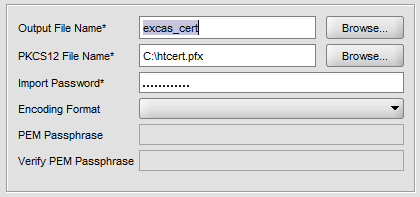
Choose your pfx file and give a name like excas_cert for local usage.
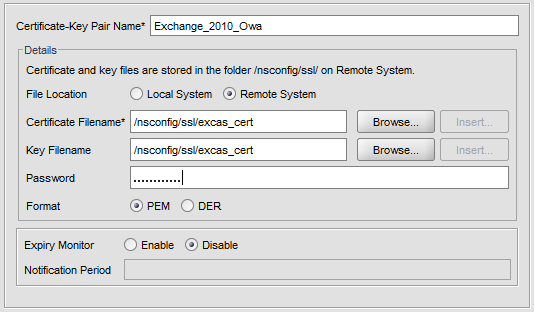
Then navigate to SSL -> Certificates and click Add.
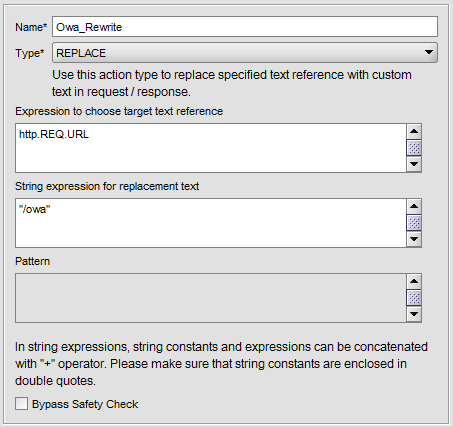
Now navigate to Rewrite -> Actions on Netscaler and click Add.
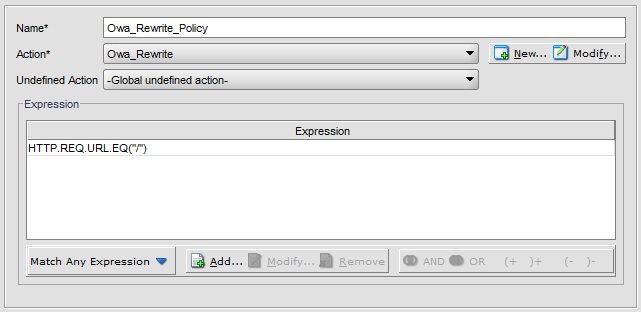
Navigate to Rewrite -> Policy and click Add.
We finished pre-required steps. Now navigate to Load Balancing -> Virtual Servers and click Add.
Give NLB IP Address. Choose SSL and port 443. Go to SSL and choose OWA certificate and click Add:
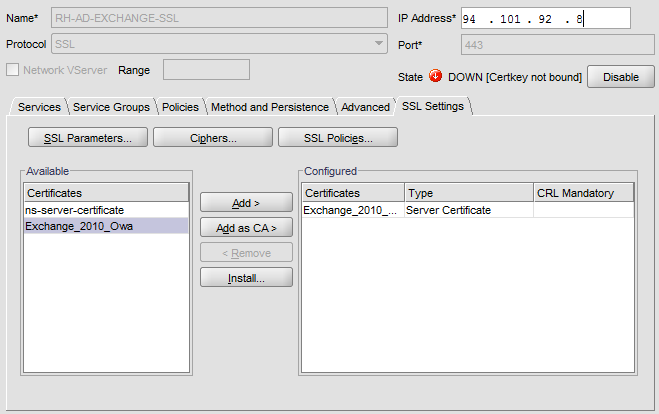
Add Owa services:

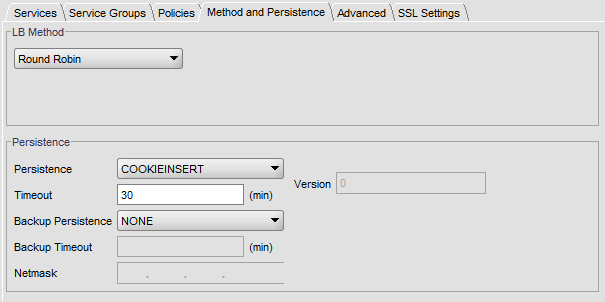
Configure Method and Persistence:
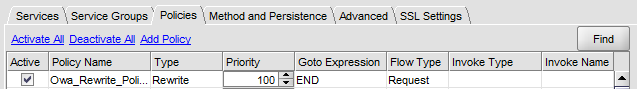
Configure OWA Redirection:
Click Create and finish SSL Virtual Server Load Balancing.
Now lets create another Virtual Server to redirect HTTP requests to HTTPS.
Navigate to Load Balancing -> Virtual Servers and click Add.
Give same NLB IP Address. Choose HTTP and port 80. Do NOT choose any service.
Go to Advanced Tab:
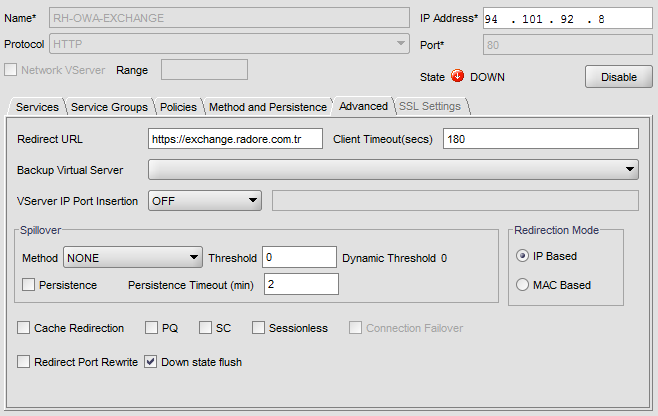
Also configure Method and Persistence:

Click Create and finish HTTP Virtual Server Load Balancing.
Because of you don’t select any service, Virtual Server should seen as Down.

Last step, go to IIS on EXCAS01 and EXCAS02. Configure SSL Security:

Clear “Require SSL” and click Accept from SSL settings. Do same things for: OWA, EWS, ECP..
All virtual directories should accept non HTTPS traffics.
Now test your Exchange Server 2010 OWA:
Wadaaaa! We finished Citrix Netscaler Load Balancing for OWA.
Next Part, We will see how to configure CAS arrays and Hub Transport server load balancing.
Thanks for reading.
Please continue with Part 4:
Hosted Exchange 2010 – Hosted Exchange 2010 Installation